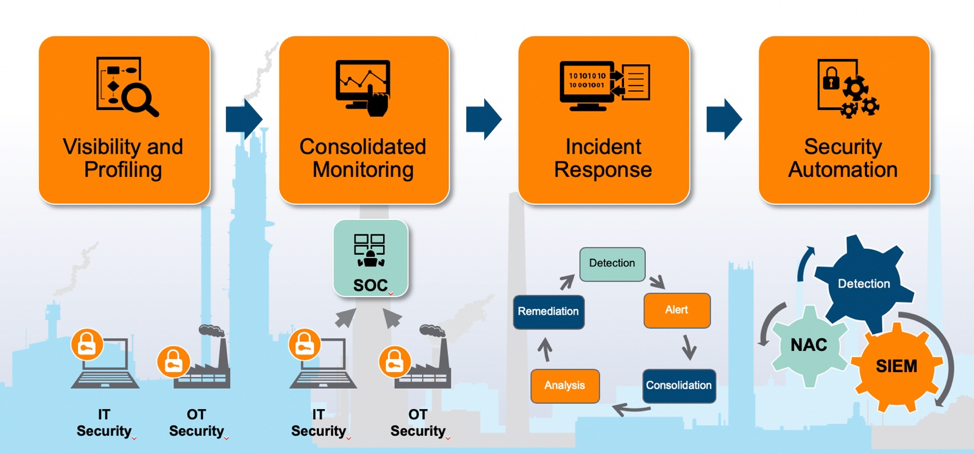
Introducing Industrial Defender ASM 7.1 with New Passive Monitoring Capabilities - Industrial Defender
Managing industrial control systems cybersecurity: Operational technology security by Deloitte and Dragos

Itris Automation ICS Monitoring, Real-time PLC Diagnostics Solution for Operators to Automation Experts :

Monitoring ICS Cyber Operation Tools and Software Exploit Modules To Anticipate Future Threats | FireEye Inc