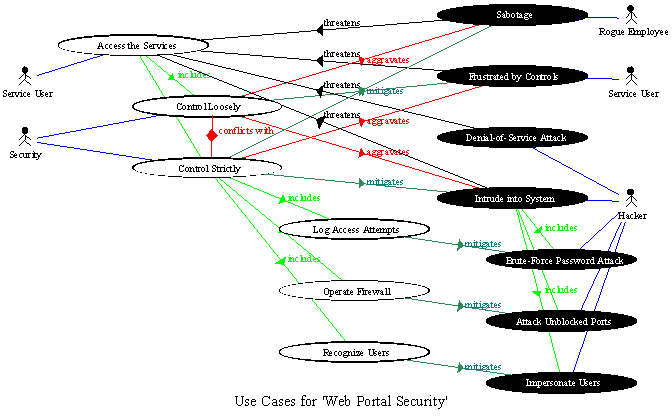
Misuse case testing - CISSP Cert Prep (2021): 6 Security Assessment and Testing Video Tutorial | LinkedIn Learning, formerly Lynda.com

Use and Misuse Cases diagram. Use cases on the left and Misuse Cases on... | Download Scientific Diagram
![PDF] An extended misuse case notation: Including vulnerabilities and the insider threat | Semantic Scholar PDF] An extended misuse case notation: Including vulnerabilities and the insider threat | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b611114e9e6f211c154678cfd758a8f8ebc69551/7-Figure4-1.png)
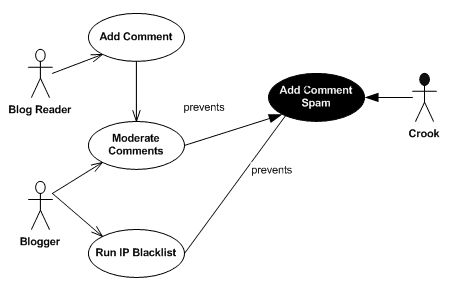

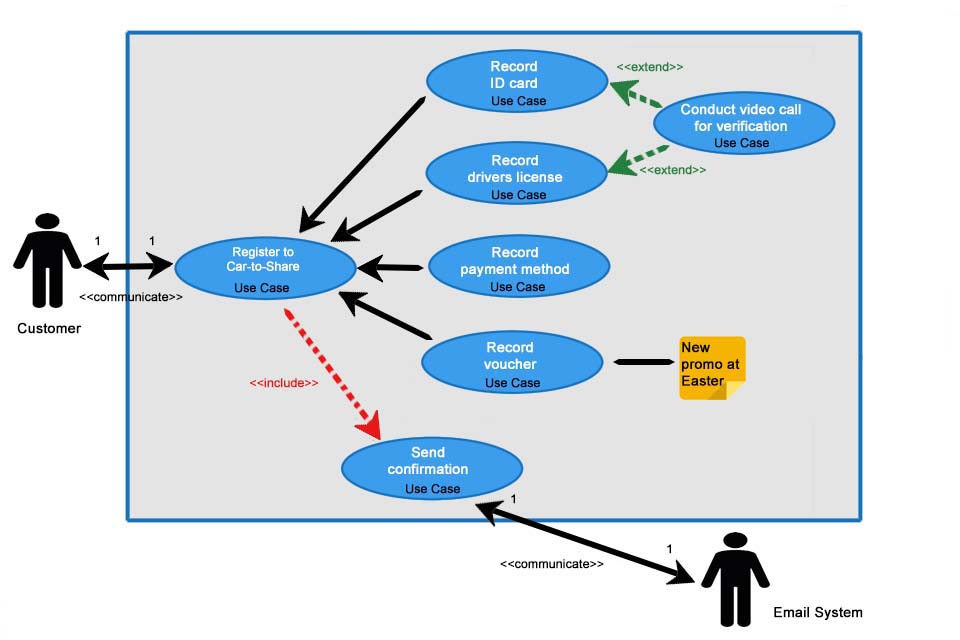

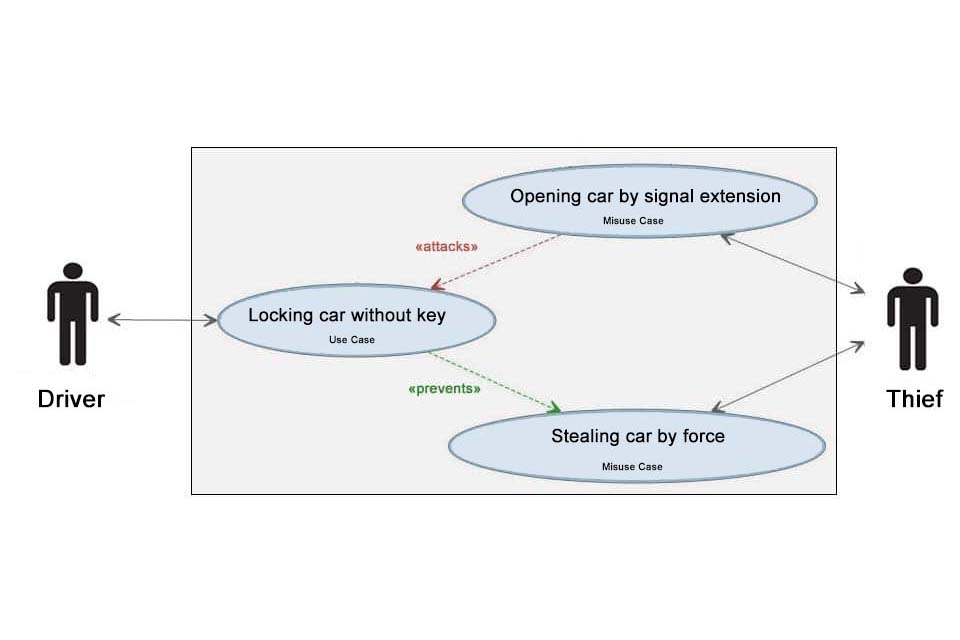


![PDF] Modelling misuse cases as a means of capturing security requirements | Semantic Scholar PDF] Modelling misuse cases as a means of capturing security requirements | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/2dccdb6a58c1f6f0f5446f3922bc87fcb471eb66/6-Figure5-1.png)